e-SIM
Since Bumblebee Technologies’ establishment Bumblebee has been steadily building a true Value Added portfolio of Solutions, tailored to the continues changing demands of its clients. As latest in this portfolio we would like to present a solution for Mobile Network Operators to successfully deploy the integration of eSIM. We understand the importance and the consequences of the long-term (radical) changes in the years to come, not just for the end-user but also and more-over for the operators.
eSim
- eUICC Explained
- eUICC Markets
- The eUICCs Remote Provisioning Server
- The hardware in eUICC is optional
- The security in eUICC
- The profile in eUICC & Multiple profiles

eUICC Explained
eUICC or eSIM is a new concept of how to issue SIMs and activate them on the network. The “e” in eUICC stands for embedded, which is not necessarily the case. A SIM like this can either be an embedded chip into a device or a plug-in SIM card, as long as it supports remote provisioning.

eUICC Markets
- Consumer devicesThe consumer device market is one of the sectors in which the development of eSIM will have a significant impact. An increasing number of devices such as, handhelds, wearables and tablets are connected and the possibility of using embedded UICCs becomes more attractive in the industry.
- Connected carsThe consumer device market is one of the sectors in which the development of eSIM will have a significant impact. An increasing number of devices such as, handhelds, wearables and tablets are connected and the possibility of using embedded UICCs becomes more attractive in the industry.
- The internet of thingsAs a substitute of human interference, an increasing number of devices are communicating with each other. These M2M devices make use of mobile network connections and show great opportunities for monitoring and improving business processes. Bumblebee Technologies is able to provide devices for amongst others, health care, vending machines, security-cameras and other connected living or controlling devices, with the ability to connect to a mobile network. More importantly, to seamlessly work together.
- General M2MWith the introduction of the embedded UICC, customers will be able to switch operators using remote provisioning. Bumblebee Technologies can provide its customers with the appropriate M2M solution. Ranging from embeddable MFF2 and SON-8 chips to plug-in eSIM, with most relevant being their Operating Systems. As well as, providing the backend server needed, to serve a ready-to use eSIM solution. All of this is conform to the GSMA’s Remote Provisioning Architecture for Embedded UICC Test Specification
The eUICCs Remote Provisioning Server
To manage the eUICCs, a secure and interoperable Remote Provisioning server is required. The Electrical Profile is encapsulated within an industry-standard syntax (ASN.1).
- On-card interfaces are standardize by SOAP web-contracts.
- On-card interfaces are standardize.
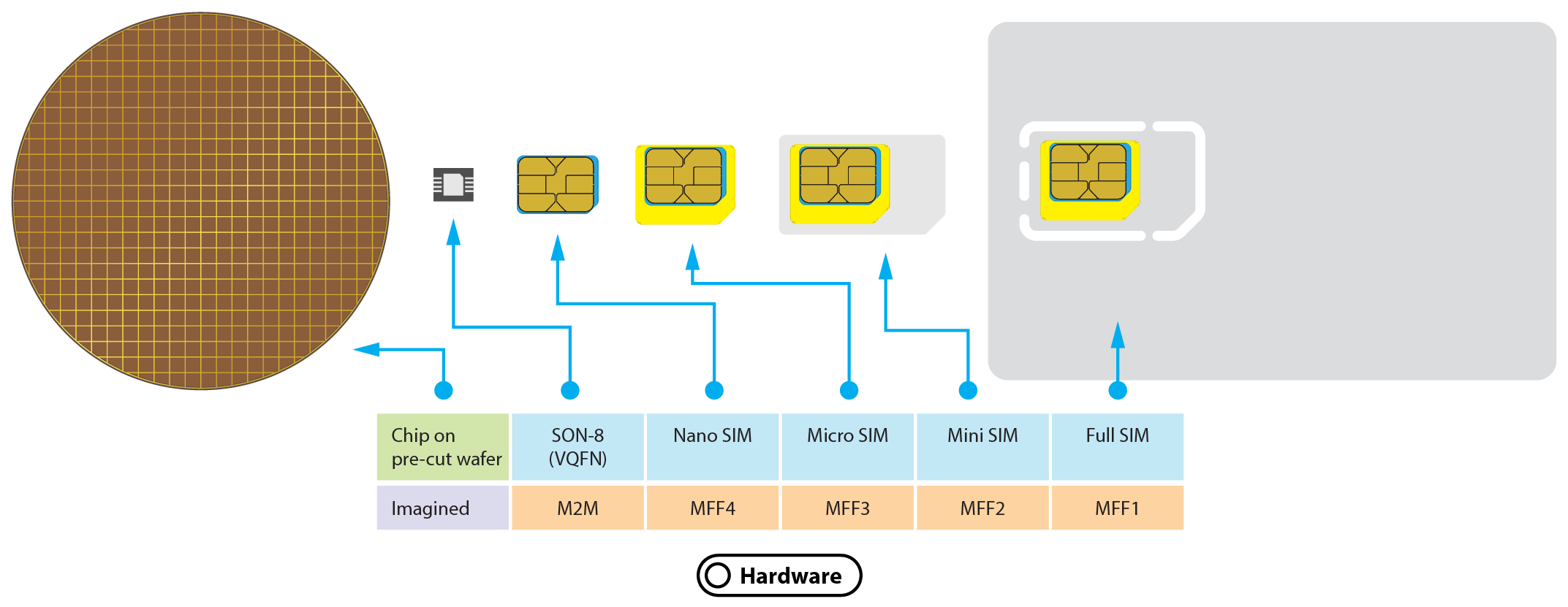
The hardware in eUICC is optional
The hardware on the module has been changed as well. A new form factor has been introduced; MFF2 or QFN8.
- 6x5mm vs 12.3x8.8m (4FF) or 25x15mm (2FF) making MFF2 the smallest chip yet.
- Deeply embedded into chipsets for security and improved logistics.
- Longer lifespan, increased resiliency in tougher operating conditions.
The security in eUICC
More stakeholders are able to access the chip, negatively influencing its security. The architecture is BSI approved with EAL 4+ Protection Profile. The need to protect both, the mobile network and its subscribers is critical.
This is an addition to the existing security standards for the life-cycle of a SIM such as Security Accreditation Scheme (SAS) and leading technologies for ciphering, integrity and perfect forward secrecy during authentication.

The profile in eUICC & Multiple profiles
- The Single ProfileThe profile stores all information about a subscriber, within a given mobile network. Secret keys to allow for secure authentication with the network, along with network-managed resident applications and a configured le system, are all stored within the electrical profile.
- Multiple ProfileseUICCs are capable of storing multiple profiles, utilizing an architecture based on Security Domains to ensure separation of Roles and Data. The chip can be deployed once, and modified indefinitely without any compromise on security. A secure architecture certified by the BSI from the GSM Association allows for interoperability.
An SM-SR manages the ISD-R (Root security domain) for secure routing. While the SM-DPs manage respective ISD-P (Prole security domains) for data preparation. Trust is established using a certificate chain, where the root CI is Symantec/GSMA.
